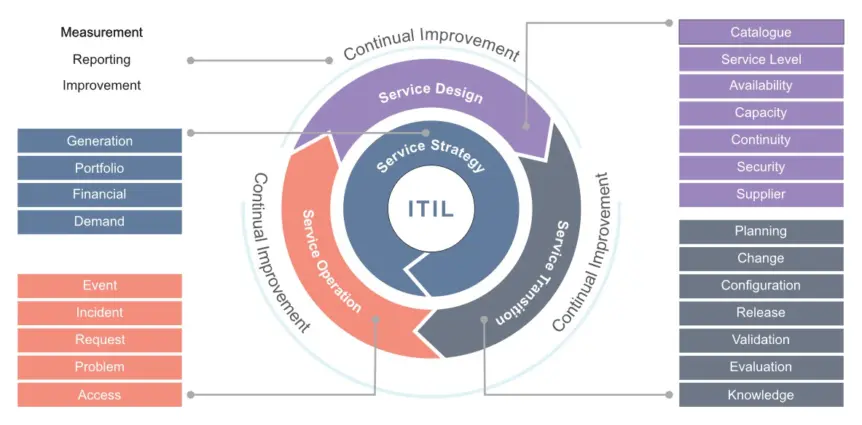
In the previous article published in the summer 2022 edition of SteamTalk, our IT Department highlighted that Information Technology plays a vital role in every company to ensure effective communication, financial management and technological progression. The Information Technology Infrastructure Library (ITIL) defines IT management as comprising five sets of best practices.
Security falls under Service Design but has a direct impact on all other areas. Cyber security has become extremely important not only for all companies but also for individuals. All data captured within IT systems such as our communication, financial or information management systems, or external systems like online banking, are protected through highly complex and well-developed security systems. Many of these systems are so well developed that attackers have given up trying to attack the security systems directly. Social engineering and malware are being used to gain access to systems.
Social engineering can be defined as deception to manipulate individuals into divulging confidential or personal information that may be used for fraud through a well disguised email or even a phone call. Malware (“malicious software”) is a file or code, typically delivered over a network or email; infects, explores, steals, or conducts virtually any behaviour an attacker wants. Once the attacker has access, information is collected and financial transactions are performed to the benefit of the attacker. The number of methods used by attackers are extensive, and that is why John Thompson has partnered with Numata Business IT to train users on cyber security and all the risks involved.
The PII Protect training platform developed and maintained by Numata Business IT has been made available to all computer users within John Thompson. All users are required to work through the training modules and complete the quizzes. Users are assigned a score depending on their performance during the training and must maintain a score above 630. Please submit an IT support ticket if you do not have
access to the PII Protect training platform.